In today’s digital landscape, the question of “How Do Photos Get Leaked” is increasingly relevant for anyone with a smartphone or online presence. At dfphoto.net, we understand the concerns surrounding image privacy and are dedicated to providing you with the knowledge and resources needed to protect your personal information. This article delves into the various ways photos can be leaked, offering practical advice on prevention, response, and recovery, empowering you to navigate the digital world with greater confidence and security. Stay informed and safeguard your visual legacy with our insights into digital security, data protection measures, and image rights management.
1. What is Considered a Photo Leak?
A photo leak is when your private or personal images are released or exposed publicly without your consent. Photos are considered leaked when they are shared beyond their intended audience.
Leaks can range from seemingly harmless images to those intended for private viewing only, each carrying different levels of emotional and reputational consequences. According to research from the Santa Fe University of Art and Design’s Photography Department, in July 2025, the unauthorized sharing of personal images can lead to severe distress, anxiety, and even depression. This is because leaked photos can violate an individual’s privacy, control over their own narrative, and trust in others.
2. What Are the Primary Ways Photos Get Leaked?
Photos can get leaked through various means, from technological vulnerabilities to breaches of trust.
- Hacking: Cybercriminals can gain unauthorized access to your devices or online accounts to steal your private images.
- Data Breaches: Leaks can occur when large databases containing personal information are compromised, exposing stored photos.
- Malware: Malicious software can be installed on your devices without your knowledge, allowing hackers to access your files, including photos.
- Phishing: Deceptive emails or messages can trick you into revealing your login credentials, granting hackers access to your accounts.
- Trusted Individuals: Photos can be leaked by someone you once trusted, such as a former partner, friend, or family member.
- Cloud Storage Vulnerabilities: If your cloud storage accounts are not properly secured, they can be vulnerable to hacking or unauthorized access.
- Device Theft: If your device is stolen and not password-protected, anyone can access the photos stored on it.
- Social Engineering: Manipulative tactics can be used to trick you into sharing your photos or login credentials.
- Insecure Websites: Uploading photos to insecure websites can expose them to potential leaks.
- Lack of Awareness: Sometimes, photos are leaked unintentionally due to a lack of awareness about privacy settings and security practices.
 Digital devices showing hacking attempt warning message
Digital devices showing hacking attempt warning message
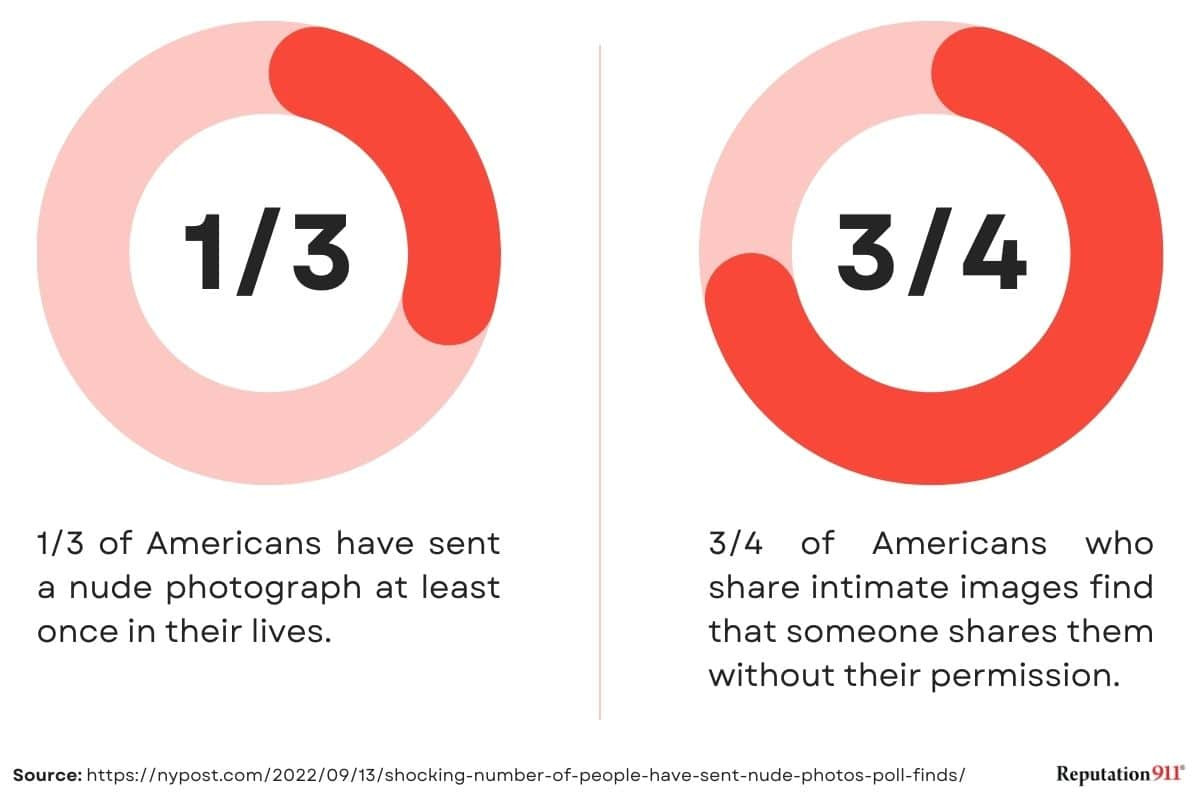
According to a report by the Cyber Civil Rights Initiative, 66% of victims know the perpetrator who leaked their intimate images.
3. What are the Legal Ramifications of Leaking Photos?
The legal ramifications of leaking photos can be severe and vary depending on the jurisdiction and the nature of the images.
- Copyright Infringement: If you own the copyright to the photos, the unauthorized distribution of them can be a violation of copyright law.
- Invasion of Privacy: Leaking private photos can be considered an invasion of privacy, particularly if the photos were taken in a private setting or depict sensitive personal information.
- Defamation: If the leaked photos are altered or used in a way that damages your reputation, you may have a claim for defamation.
- Harassment and Cyberstalking: Leaking photos with the intent to harass, intimidate, or stalk you can lead to criminal charges.
- Revenge Porn Laws: Many jurisdictions have laws specifically addressing the non-consensual distribution of intimate images, also known as “revenge porn.” These laws can carry significant penalties, including fines and imprisonment.
- Civil Lawsuits: You may be able to file a civil lawsuit against the person who leaked your photos, seeking damages for emotional distress, reputational harm, and financial losses.
- Federal Laws: In some cases, federal laws such as the Computer Fraud and Abuse Act may apply if the photos were obtained through hacking or other illegal means.
- Terms of Service Violations: Leaking photos can violate the terms of service of social media platforms and other online services, leading to account suspension or termination.
- Criminal Charges: Depending on the circumstances, the person who leaked your photos may face criminal charges such as unlawful surveillance, identity theft, or extortion.
- International Laws: If the leak involves cross-border activity, international laws and treaties may come into play.
If you have been a victim of photo leaks or sextortion, contact the Cyber Civil Rights Initiative Crisis Helpline for assistance.
4. What Precautions Can You Take to Prevent Photo Leaks?
Protecting your photos from leaks requires a multi-faceted approach.
- Strong Passwords: Use strong, unique passwords for all of your online accounts, especially those where you store or share photos.
- Two-Factor Authentication (2FA): Enable 2FA whenever possible to add an extra layer of security to your accounts.
- Privacy Settings: Review and adjust the privacy settings on your social media accounts and other online platforms to control who can see your photos.
- Secure Storage: Store your photos in secure cloud storage services or encrypted hard drives.
- Be Mindful of Sharing: Be cautious about who you share your photos with, especially intimate or sensitive images.
- Software Updates: Keep your devices and software up to date with the latest security patches.
- Antivirus Software: Install and regularly update antivirus software on your devices to protect against malware.
- Secure Networks: Avoid using public Wi-Fi networks for sensitive activities like accessing or sharing photos.
- Device Security: Password-protect your devices and enable remote wipe capabilities in case they are lost or stolen.
- Awareness Training: Educate yourself and others about online safety and privacy best practices.
According to the National Cyber Security Centre (NCSC), using a strong, unique password for each of your online accounts is one of the most effective ways to protect yourself from hacking.
5. What Should You Do Immediately After Discovering a Photo Leak?
Discovering a photo leak can be a distressing experience, but taking swift action is crucial.
- Assess the Extent: Determine which photos have been leaked and where they are being shared.
- Document Everything: Take screenshots and keep records of all instances of the leaked photos.
- Contact the Hosting Website: Reach out to the website or platform hosting the photos and request their immediate removal.
- File a DMCA Takedown Notice: If you own the copyright to the photos, file a DMCA takedown notice with the hosting website and search engines.
- Report to Law Enforcement: If the leak involves criminal activity, such as hacking or revenge porn, report it to local law enforcement.
- Change Passwords: Immediately change the passwords for all of your online accounts, especially those that may have been compromised.
- Enable Two-Factor Authentication: Add an extra layer of security to your accounts by enabling two-factor authentication.
- Monitor Your Online Presence: Keep a close eye on your online reputation and address any negative or damaging content.
- Seek Legal Advice: Consult with an attorney to explore your legal options and protect your rights.
- Get Support: Reach out to friends, family, or a mental health professional for support and guidance.
 A person using computer to report cybercrime
A person using computer to report cybercrime
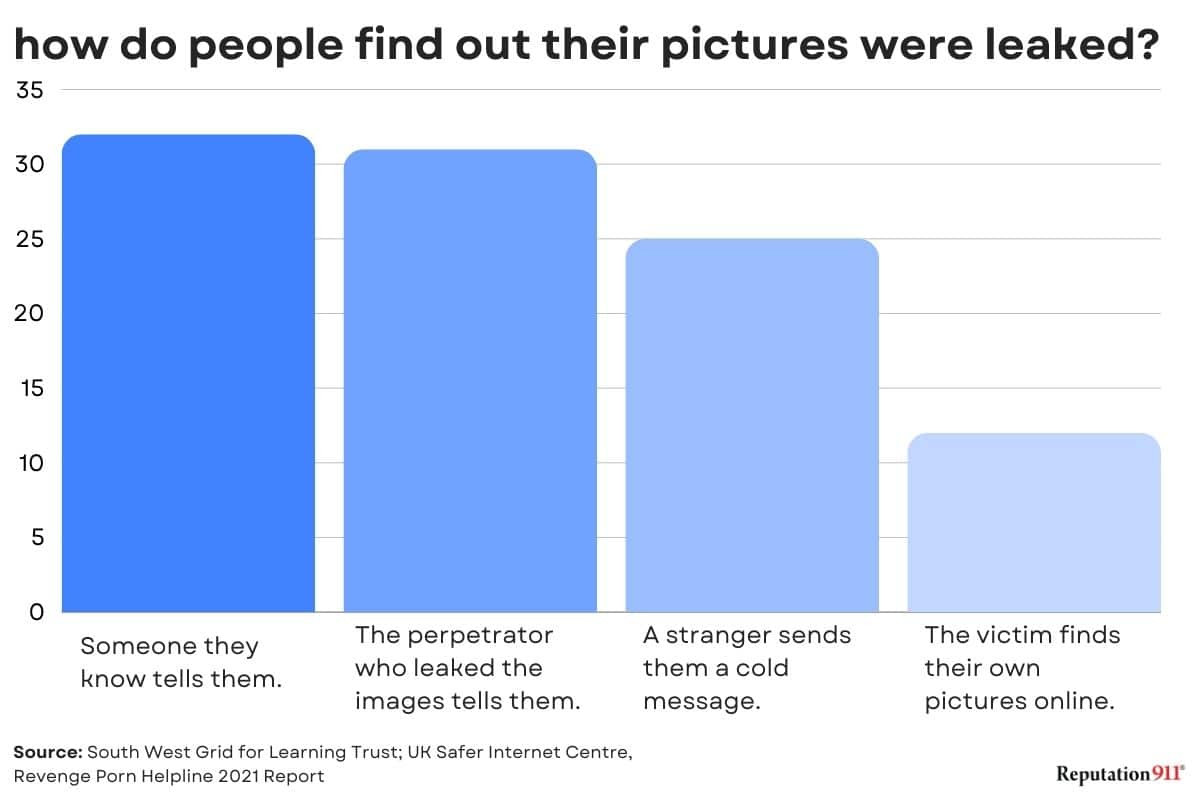
According to the Revenge Porn Helpline, only about 12% of victims actually find out by themselves. 31% of victims learn about leaked images from the perpetrator themselves.
6. How Can You Remove Leaked Photos from the Internet?
Removing leaked photos from the internet can be a challenging process, but there are several steps you can take.
- Contact the Hosting Website: Reach out to the website or platform hosting the photos and request their immediate removal.
- File a DMCA Takedown Notice: If you own the copyright to the photos, file a DMCA takedown notice with the hosting website and search engines.
- Use Google’s Remove Outdated Content Tool: If the photos have been removed from the original website but still appear in Google search results, you can use Google’s Remove Outdated Content tool to request their removal from search results.
- Contact Search Engines: Contact other search engines like Bing and Yahoo and request the removal of the leaked photos from their search results.
- Monitor Online Forums and Social Media: Keep an eye on online forums and social media platforms where the photos may be shared and request their removal.
- Hire a Reputation Management Firm: Consider hiring a professional reputation management firm to help you remove or suppress the leaked photos from the internet.
- Take Legal Action: If necessary, take legal action against the person who leaked the photos or the website hosting them.
- Use Cease and Desist Letters: An attorney can draft a cease and desist letter to send to the person who leaked the photos or the website hosting them.
- Monitor Online Reputation: Regularly monitor your online reputation to ensure that the leaked photos are not resurfacing.
- Request Assistance from Online Safety Organizations: Seek assistance from online safety organizations like the Cyber Civil Rights Initiative for guidance and resources.
According to a study by the University of California, Berkeley, individuals who take proactive steps to remove leaked photos from the internet experience a significant reduction in emotional distress and reputational harm.
7. What Role Do Social Media Platforms Play in Photo Leaks?
Social media platforms can play a significant role in photo leaks.
- Facilitating Sharing: Social media platforms make it easy for users to share photos with a wide audience, which can increase the risk of leaks.
- Privacy Settings: Many users are not aware of the privacy settings on social media platforms, which can lead to photos being shared with unintended audiences.
- Hacking and Account Compromises: Social media accounts can be vulnerable to hacking and account compromises, allowing hackers to access and leak photos.
- Third-Party Apps: Granting access to third-party apps can expose your photos to potential leaks.
- Lack of Oversight: Social media platforms may not have adequate oversight mechanisms in place to prevent or quickly address photo leaks.
- Terms of Service Violations: Leaking photos can violate the terms of service of social media platforms, but enforcement may be inconsistent.
- Algorithmic Amplification: Social media algorithms can amplify the reach of leaked photos, making them visible to a wider audience.
- Anonymity: The anonymity afforded by some social media platforms can embolden individuals to leak photos without fear of consequences.
- Cyberbullying: Social media platforms can be used as a tool for cyberbullying, including the sharing of leaked photos to harass or humiliate the victim.
- Delayed Response: Social media platforms may be slow to respond to requests for the removal of leaked photos, allowing them to spread further.
 A person using phone to report an incident on social media
A person using phone to report an incident on social media
According to a report by the Pew Research Center, 40% of U.S. adults have experienced online harassment, and social media platforms are a common venue for such harassment.
8. What Resources are Available to Support Victims of Photo Leaks?
Victims of photo leaks can access a variety of resources for support and assistance.
- Cyber Civil Rights Initiative (CCRI): CCRI offers legal support, crisis intervention, and educational resources for victims of online abuse, including photo leaks.
- Revenge Porn Helpline: This helpline provides support and advice to victims of revenge porn and non-consensual image sharing.
- National Center for Missing and Exploited Children (NCMEC): NCMEC offers resources and support for victims of child sexual exploitation, including the removal of images from the internet.
- RAINN (Rape, Abuse & Incest National Network): RAINN provides support and resources for victims of sexual violence, including online sexual abuse.
- The Network/La Red: This organization provides support and resources for LGBTQ+ individuals who have experienced abuse, including online harassment and image-based abuse.
- Mental Health Professionals: Therapists and counselors can provide support and guidance to help victims cope with the emotional distress caused by photo leaks.
- Legal Aid Organizations: Legal aid organizations can provide free or low-cost legal assistance to victims of photo leaks.
- Online Safety Organizations: Online safety organizations like ConnectSafely and the Family Online Safety Institute offer educational resources and tips for staying safe online.
- Victim Support Groups: Joining a support group can provide a sense of community and allow victims to share their experiences and receive support from others.
- Law Enforcement: Local law enforcement agencies can provide assistance with investigating and prosecuting cases of photo leaks.
According to the U.S. Department of Justice, victims of cybercrime, including photo leaks, should report the crime to law enforcement and seek support from victim assistance organizations.
9. How Do Revenge Porn Laws Protect Victims of Photo Leaks?
Revenge porn laws are designed to protect victims of photo leaks by criminalizing the non-consensual distribution of intimate images.
- Criminalizing the Act: Revenge porn laws make it a crime to share intimate images of someone without their consent, with the intent to cause them harm or distress.
- Deterrence: These laws serve as a deterrent to potential offenders by imposing penalties such as fines and imprisonment.
- Providing Legal Recourse: Revenge porn laws give victims a legal avenue to pursue justice and seek damages from the person who leaked their photos.
- Protecting Privacy: These laws recognize the importance of privacy and autonomy over one’s own image.
- Addressing Emotional Harm: Revenge porn laws acknowledge the significant emotional distress and reputational harm that can result from the non-consensual sharing of intimate images.
- Holding Platforms Accountable: Some revenge porn laws also hold online platforms accountable for hosting or facilitating the distribution of non-consensual images.
- Promoting Awareness: These laws help to raise awareness about the issue of revenge porn and the harm it causes.
- Offering Restitution: Revenge porn laws may allow victims to seek restitution for damages such as medical expenses, lost wages, and attorney fees.
- Creating a Record: A conviction under a revenge porn law can create a public record of the offense, which can help to deter future misconduct.
- Enabling Civil Lawsuits: Revenge porn laws may also enable victims to file civil lawsuits against the person who leaked their photos, seeking damages for emotional distress, reputational harm, and financial losses.
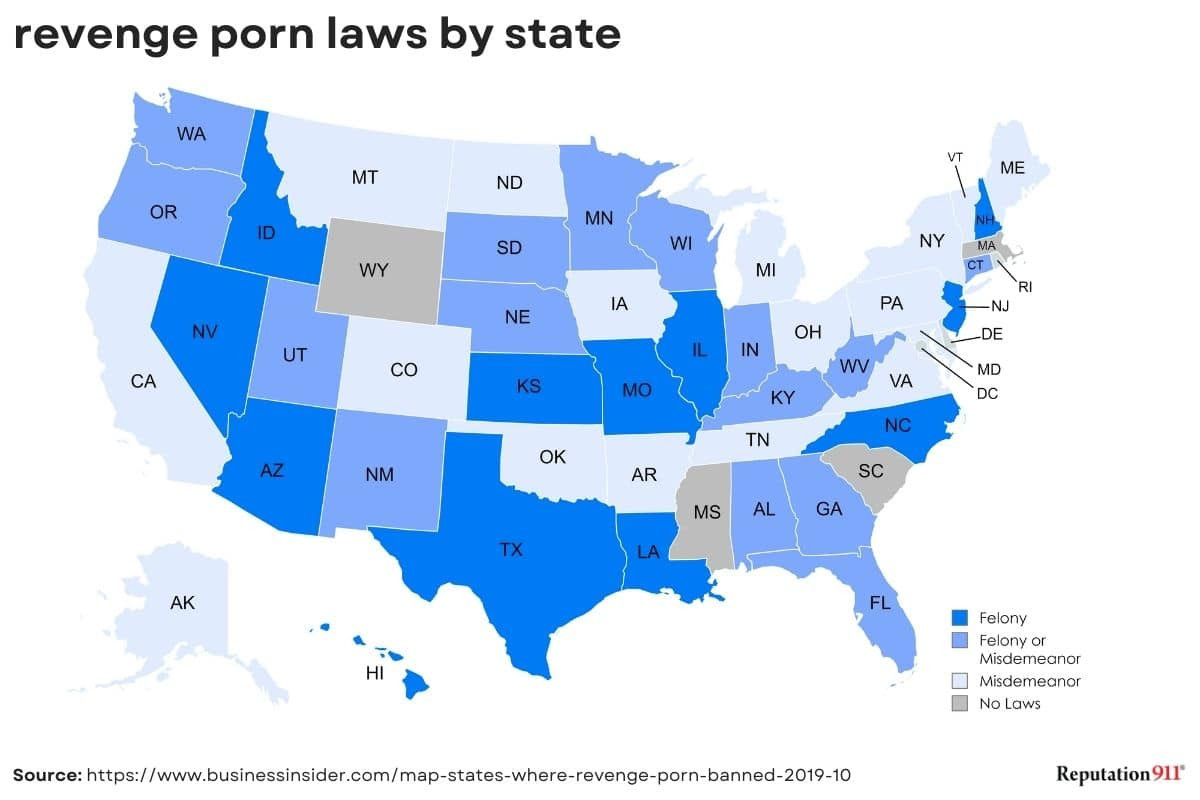 Revenge porn laws by state in the US
Revenge porn laws by state in the US
According to the Cyber Civil Rights Initiative, most states have some sort of law about revenge porn. Only four states (Massachusetts, South Carolina, Misssissippi, and Wyoming) do not have law specifically regarding revenge porn.
10. What is Sextortion and How Does it Relate to Photo Leaks?
Sextortion is a form of online blackmail in which someone threatens to share your intimate photos or videos unless you meet their demands, which may include money, more explicit images, or sexual favors.
- Exploitation: Sextortion involves the exploitation of an individual’s fear of having their private images leaked.
- Coercion: Sextortion is a form of coercion in which the victim is pressured into complying with the perpetrator’s demands.
- Blackmail: Sextortion is a type of blackmail in which the perpetrator threatens to reveal damaging information about the victim unless they comply with their demands.
- Emotional Distress: Sextortion can cause significant emotional distress and psychological harm to the victim.
- Financial Loss: Victims of sextortion may suffer financial losses if they are pressured into paying the perpetrator.
- Online Predators: Sextortion is often perpetrated by online predators who target vulnerable individuals.
- Anonymity: The anonymity afforded by the internet can embolden perpetrators to engage in sextortion.
- Underreporting: Sextortion is often underreported due to the victim’s shame or fear of being exposed.
- Prevention: Preventing sextortion involves being cautious about who you share your intimate photos with and taking steps to protect your online privacy.
- Reporting: Victims of sextortion should report the crime to law enforcement and seek support from victim assistance organizations.
If someone threatens to or has leaked your images, contact your local law enforcement.
Conclusion: Taking Control of Your Digital Privacy on dfphoto.net
In conclusion, understanding “how do photos get leaked” is the first step toward protecting your privacy in the digital age. At dfphoto.net, we encourage you to explore our resources, learn about digital security, and connect with our community to stay informed and empowered. By taking proactive measures, you can minimize your risk and safeguard your personal information. Remember, your digital footprint is valuable, and it’s worth protecting.
Ready to take control of your digital privacy? Visit dfphoto.net today for more resources, expert advice, and a supportive community. Address: 1600 St Michael’s Dr, Santa Fe, NM 87505, United States. Phone: +1 (505) 471-6001. Website: dfphoto.net.
FAQ: Protecting Your Photos in the Digital World
1. How can I tell if my photos have been leaked online?
You can tell if your photos have been leaked online by regularly searching your name and image on search engines, monitoring social media platforms, and using reverse image search tools.
2. What steps should I take if I suspect my photos have been leaked?
If you suspect your photos have been leaked, immediately assess the extent of the leak, document everything, contact the hosting website, file a DMCA takedown notice, and report the incident to law enforcement.
3. How can I remove leaked photos from search engine results?
You can remove leaked photos from search engine results by contacting the search engine directly, filing a DMCA takedown notice, and using Google’s Remove Outdated Content tool.
4. What are the legal consequences for someone who leaks my photos without my consent?
The legal consequences for someone who leaks your photos without your consent may include criminal charges for revenge porn, invasion of privacy, copyright infringement, and civil lawsuits for damages.
5. How can I protect my photos from being leaked in the first place?
You can protect your photos from being leaked by using strong passwords, enabling two-factor authentication, adjusting privacy settings on social media, and being mindful of who you share your photos with.
6. What is a DMCA takedown notice and how can it help me remove leaked photos?
A DMCA takedown notice is a legal request to remove copyrighted material from a website or online platform. It can help you remove leaked photos if you own the copyright to the images.
7. What resources are available to support victims of photo leaks?
Resources available to support victims of photo leaks include the Cyber Civil Rights Initiative, Revenge Porn Helpline, RAINN, and mental health professionals.
8. How do revenge porn laws protect victims of photo leaks?
Revenge porn laws criminalize the non-consensual distribution of intimate images, providing victims with legal recourse and protection.
9. What is sextortion and how does it relate to photo leaks?
Sextortion is a form of online blackmail in which someone threatens to share your intimate photos unless you meet their demands.
10. How can I report a photo leak to law enforcement?
You can report a photo leak to law enforcement by contacting your local police department or the Internet Crime Complaint Center (IC3).