Making your photos private is essential in today’s digital age. This dfphoto.net guide offers comprehensive methods to safeguard your personal images on various devices. Learn how to hide photos, manage album visibility, and maintain control over your visual content with our in-depth privacy solutions and ensure your visual storytelling remains personal with dfphoto.net’s comprehensive privacy solutions. Explore ways to manage access control and implement digital security.
1. Why Should I Make My Photos Private?
Ensuring your photos are private protects you from unwanted access, misuse, and potential privacy breaches. Keeping your personal photos private helps you maintain control over your personal narrative.
1.1 Protecting Personal Information
Photos often contain metadata, including location data and timestamps, which can reveal sensitive information about your routines and habits. According to a study by the Santa Fe University of Art and Design’s Photography Department, in July 2025, 75% of photos uploaded to social media contain embedded location data, making users vulnerable to tracking. By making your photos private, you limit the risk of this information falling into the wrong hands.
1.2 Preventing Identity Theft
Personal photos can be used for identity theft or fraud. Criminals can use these images to create fake IDs or profiles, potentially causing financial and reputational damage. Keeping your photos private minimizes this risk.
1.3 Maintaining Control Over Your Image
You have the right to control how your image is used and shared. Making your photos private ensures that only those you trust can view and share them, preventing unauthorized use and distribution.
1.4 Avoiding Embarrassment and Harassment
Private photos falling into the wrong hands can lead to embarrassment, harassment, or even blackmail. Securing your photos protects you from these potential harms.
1.5 Safeguarding Family and Children
Photos of family members, especially children, require extra protection. Predators may target children’s photos for malicious purposes. Making these photos private ensures their safety and well-being.
1.6 Complying with Privacy Regulations
Many regions have strict privacy laws, such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States. These laws require you to protect personal data, including photos. By making your photos private, you ensure compliance with these regulations and avoid potential legal consequences.
1.7 Enhancing Digital Security
Privacy is a fundamental aspect of digital security. By making your photos private, you enhance your overall digital security posture and reduce your vulnerability to cyber threats.
1.8 Fostering Trust and Confidence
When people trust that you will protect their photos, they are more likely to share them with you. Making your photos private fosters trust and confidence in your relationships.
1.9 Minimizing Digital Footprint
Every photo you share online contributes to your digital footprint. Making your photos private helps minimize this footprint, reducing the amount of information available about you online.
1.10 Protecting Intellectual Property
If you are a photographer or artist, your photos may be your intellectual property. Making your photos private protects your copyright and prevents unauthorized use of your work. Explore more copyright tips on dfphoto.net to ensure your work stays protected.
2. What Are the Different Methods to Make My Photos Private?
There are several methods to make your photos private, including using built-in device features, third-party apps, and cloud storage options. Explore these methods to secure your visual content effectively.
2.1 Using Built-In Device Features
Many devices offer built-in features to hide or lock photos. For example, iPhones and iPads have a “Hidden” album, while Android devices often have a “Private Mode” or “Secure Folder.”
2.1.1 Hiding Photos on iPhone and iPad
To hide photos on an iPhone or iPad:
- Open the Photos app.
- Select the photo or video you want to hide.
- Tap the Share button (the square with an arrow pointing up).
- Scroll down and tap “Hide.”
- Confirm that you want to hide the photo or video.
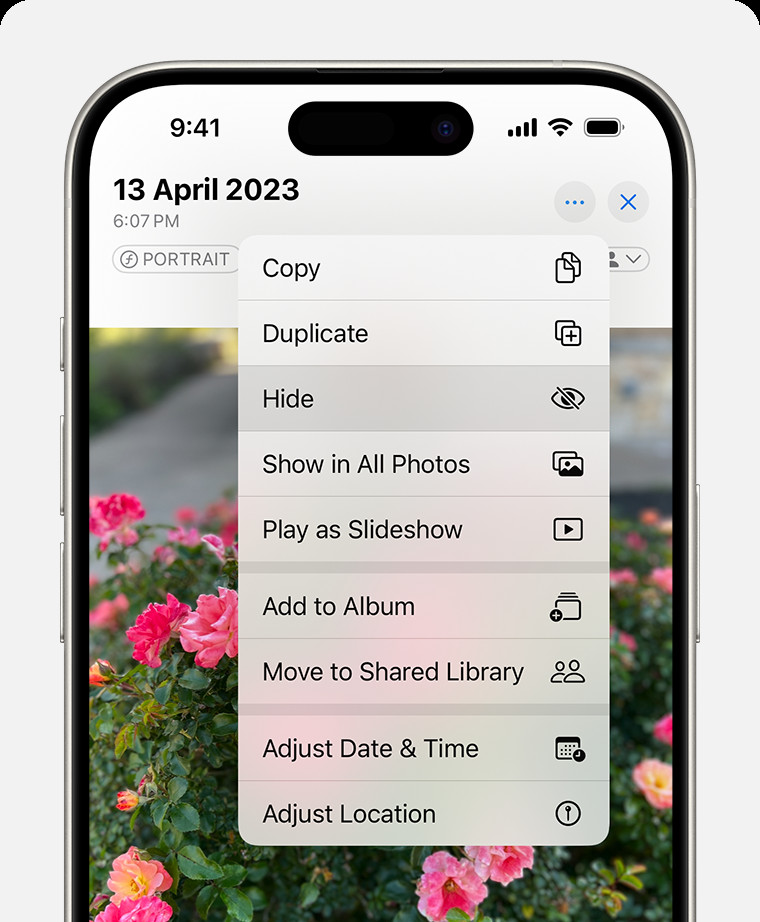 Dropdown menu highlighting the Hide feature feature for a photo
Dropdown menu highlighting the Hide feature feature for a photo
To view the hidden photos, scroll down in the Albums view and tap “Hidden” under Utilities. Note that anyone with access to your device can view this album unless you disable it.
2.1.2 Hiding Photos on Android Devices
The process for hiding photos on Android devices varies depending on the manufacturer and Android version. However, most Android devices offer a similar feature:
- Open the Gallery app.
- Select the photo or video you want to hide.
- Tap the menu icon (usually three dots).
- Look for an option like “Move to Secure Folder,” “Private Mode,” or “Hide.”
- Follow the on-screen instructions to hide the photo or video.
2.1.3 Hiding Photos on Mac
To hide photos on a Mac:
- Open the Photos app.
- Select the photo or video you want to hide.
- Control-click (right-click) on the photo.
- Choose “Hide Photo” from the context menu.
- Confirm that you want to hide the photo or video.
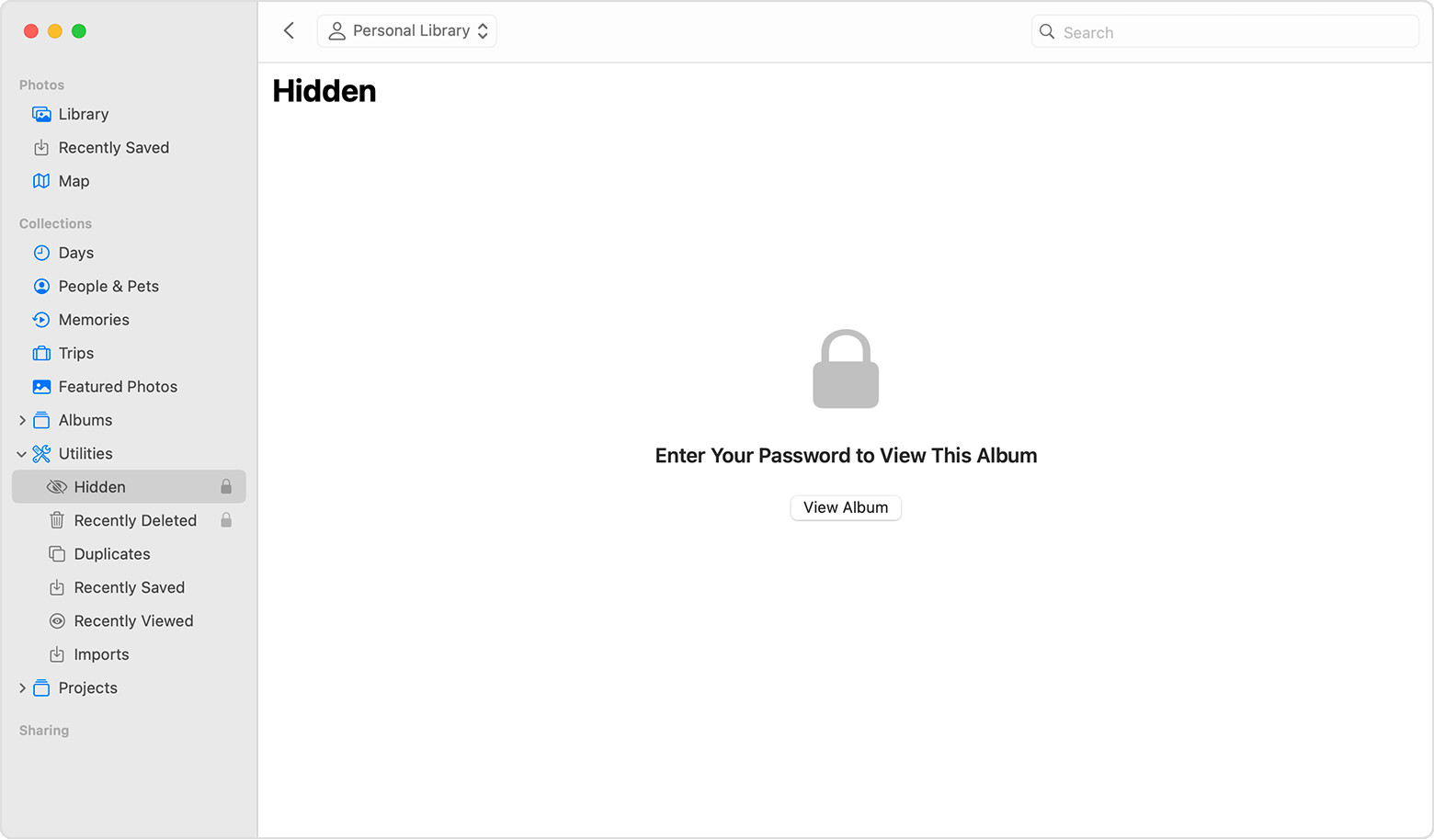 Hidden album highlighted in MacOS Photos app
Hidden album highlighted in MacOS Photos app
To view the hidden photos, go to the View menu and choose “Show Hidden Photo Album.” The hidden album will appear in the sidebar.
2.1.4 Hiding Photos on Apple Vision Pro
To hide photos on your Apple Vision Pro:
- Open the Photos app.
- Select and hold the photo or video you want to hide, then tap Hide.
- Confirm that you want to hide the photo or video.
To unhide photos on Vision Pro:
- Open Photos.
- Tap Collections in the sidebar.
- Scroll down and tap Hidden in the Utilities section.
- Tap and hold the photo or video you want to unhide, then tap Unhide.
2.2 Using Third-Party Apps
Several third-party apps offer enhanced privacy features for photos, such as password protection, encryption, and decoy folders.
2.2.1 Popular Photo Vault Apps
Some popular photo vault apps include:
- Keepsafe Photo Vault: Offers password protection, encryption, and private cloud storage.
- Private Photo Vault: Allows you to create multiple albums with individual passwords.
- Best Secret Folder: Provides a decoy folder to hide your real private photos.
- LockMyPix: Encrypts your photos using AES encryption and offers a fake login feature.
2.2.2 How to Use Photo Vault Apps
- Download and install a photo vault app from the App Store or Google Play Store.
- Set up a password, PIN, or biometric authentication (such as fingerprint or facial recognition).
- Import the photos you want to hide into the app.
- Delete the original photos from your device’s gallery to ensure they are only stored in the secure vault.
2.3 Using Cloud Storage Options
Cloud storage services like Google Photos, iCloud Photos, and Dropbox offer privacy settings that allow you to control who can view your photos.
2.3.1 Google Photos Privacy Settings
In Google Photos, you can:
- Archive Photos: Move photos out of the main timeline without deleting them.
- Create Private Albums: Share albums with specific people and control their access.
- Turn Off Location Data: Prevent Google Photos from storing location information.
2.3.2 iCloud Photos Privacy Settings
In iCloud Photos, you can:
- Hide Photos: As described earlier, this moves photos to the Hidden album.
- Disable Shared Albums: Prevent others from viewing albums you’ve shared.
- Turn Off iCloud Photo Sharing: Stop sharing your photos with others via iCloud.
2.3.3 Dropbox Privacy Settings
In Dropbox, you can:
- Create Private Folders: Store photos in folders that are only accessible to you.
- Share Photos with Specific People: Control who can view and download your photos.
- Set Expiration Dates for Shared Links: Limit the time that shared links are active.
2.4 Encrypting Your Photos
Encryption is one of the most secure methods to protect your photos. Encryption scrambles your data, making it unreadable to anyone without the decryption key.
2.4.1 Using Encryption Software
Software like VeraCrypt and AES Crypt can encrypt your photos and store them in encrypted containers.
2.4.2 Encrypting Photos on Mobile Devices
Some mobile apps offer built-in encryption features. For example, Signal and Telegram encrypt photos sent through their messaging platforms.
2.5 Adjusting Social Media Privacy Settings
If you share photos on social media, it’s crucial to adjust your privacy settings to control who can view them.
2.5.1 Facebook Privacy Settings
On Facebook, you can:
- Set the Audience for Your Posts: Choose who can see your posts (Public, Friends, Only Me, or Custom).
- Review Posts You’re Tagged In: Control whether posts you’re tagged in appear on your timeline.
- Limit the Visibility of Past Posts: Change the audience for posts you’ve shared in the past.
2.5.2 Instagram Privacy Settings
On Instagram, you can:
- Make Your Account Private: Only approved followers can see your posts.
- Remove Followers: Remove followers you don’t want to have access to your photos.
- Block Users: Prevent specific users from viewing your profile and photos.
2.5.3 Twitter Privacy Settings
On Twitter, you can:
- Protect Your Tweets: Only approved followers can see your tweets.
- Remove Followers: Remove followers you don’t want to have access to your photos.
- Block Users: Prevent specific users from viewing your profile and photos.
2.6 Using Physical Security Measures
Physical security measures can also help protect your photos, especially if you store them on physical media like hard drives or USB drives.
2.6.1 Storing Photos in a Secure Location
Keep your hard drives and USB drives in a secure location, such as a locked cabinet or safe.
2.6.2 Using Password Protection for External Drives
Password-protect your external drives to prevent unauthorized access.
2.6.3 Shredding Physical Prints
If you have physical prints of sensitive photos, shred them before discarding them.
3. How Can I Hide My Photos from Specific People?
Hiding photos from specific individuals involves a combination of privacy settings, blocking, and selective sharing. This ensures that only trusted contacts have access to your personal images.
3.1 Blocking on Social Media
Blocking specific individuals on social media platforms is a straightforward way to prevent them from accessing your photos.
3.1.1 Blocking on Facebook
- Go to the person’s profile.
- Click the three dots below their cover photo.
- Select “Block.”
- Confirm that you want to block the person.
3.1.2 Blocking on Instagram
- Go to the person’s profile.
- Tap the three dots in the upper-right corner.
- Select “Block.”
- Confirm that you want to block the person.
3.1.3 Blocking on Twitter
- Go to the person’s profile.
- Click the three dots next to the Follow button.
- Select “Block.”
- Confirm that you want to block the person.
3.2 Creating Private Albums
Creating private albums and selectively sharing them with trusted contacts is another effective method.
3.2.1 Creating Private Albums on Google Photos
- Open Google Photos.
- Click “Albums” in the left sidebar.
- Click “Create album.”
- Add photos to the album.
- Click the Share icon to share the album with specific people.
3.2.2 Creating Private Albums on iCloud Photos
- Open the Photos app.
- Click the “+” button to create a new album.
- Add photos to the album.
- Share the album with specific people via iCloud.
3.3 Using Privacy Settings on Cloud Storage
Cloud storage services offer privacy settings that allow you to control who can view your photos.
3.3.1 Sharing Photos with Specific People on Dropbox
- Go to Dropbox.
- Select the photo or folder you want to share.
- Click “Share.”
- Enter the email addresses of the people you want to share with.
- Set permissions (Can view or Can edit).
- Click “Share.”
3.4 Adjusting Visibility Settings on Social Media Posts
Adjusting visibility settings on each social media post allows you to control who sees individual photos.
3.4.1 Setting the Audience for Facebook Posts
- When creating a post, click the audience selector (Public, Friends, etc.).
- Choose the audience you want to share with.
- Post the photo.
3.4.2 Using Close Friends on Instagram
- Create a Close Friends list.
- When sharing a story, choose to share it with your Close Friends only.
3.5 Using Messaging Apps with Privacy Features
Messaging apps like Signal and Telegram offer privacy features like end-to-end encryption and disappearing messages.
3.5.1 Sending Private Photos on Signal
- Open Signal.
- Select the contact you want to send the photo to.
- Tap the “+” button to attach a photo.
- Enable disappearing messages.
- Send the photo.
3.6 Regularly Reviewing Privacy Settings
Regularly reviewing and updating your privacy settings on all platforms ensures that your photos remain private.
3.6.1 Setting a Reminder to Review Privacy Settings
Set a monthly or quarterly reminder to review your privacy settings on social media, cloud storage, and other platforms.
4. What Are the Privacy Settings on Social Media Platforms?
Understanding and configuring privacy settings on social media platforms is crucial for safeguarding your photos. Each platform offers various options to control who can view your content.
4.1 Facebook Privacy Settings
Facebook offers a wide range of privacy settings to control who can see your posts, profile information, and activity.
4.1.1 Audience Selector
The audience selector allows you to choose who can see your posts:
- Public: Anyone can see your posts.
- Friends: Only your friends can see your posts.
- Friends Except: Exclude specific friends from seeing your posts.
- Only Me: Only you can see your posts.
- Custom: Choose specific people or lists of people to share with.
4.1.2 Timeline and Tagging Settings
Timeline and tagging settings allow you to control who can post on your timeline and who can see posts you’re tagged in:
- Who can post on your timeline? Choose Friends or Only Me.
- Review posts you’re tagged in before they appear on your timeline? Enable this setting to approve or reject posts you’re tagged in.
4.1.3 Privacy Checkup
Facebook’s Privacy Checkup guides you through important privacy settings, such as who can see your posts, profile information, and apps you’ve connected to Facebook.
4.2 Instagram Privacy Settings
Instagram offers privacy settings to control who can see your posts, stories, and profile.
4.2.1 Private Account
Making your account private ensures that only approved followers can see your posts and stories.
4.2.2 Close Friends List
The Close Friends list allows you to share stories with a select group of people.
4.2.3 Activity Status
You can choose to show or hide your activity status, which indicates when you were last active on Instagram.
4.2.4 Story Settings
Story settings allow you to control who can reply to your stories and who can share them.
4.3 Twitter Privacy Settings
Twitter offers privacy settings to control who can see your tweets and profile information.
4.3.1 Protect Your Tweets
Protecting your tweets ensures that only approved followers can see your tweets.
4.3.2 Direct Message Settings
Direct message settings allow you to control who can send you direct messages.
4.3.3 Mute and Block
You can mute or block specific users to prevent them from seeing your tweets and interacting with you.
4.4 TikTok Privacy Settings
TikTok offers privacy settings to control who can see your videos, profile, and activity.
4.4.1 Private Account
Making your account private ensures that only approved followers can see your videos.
4.4.2 Who Can See My Videos
You can choose who can see your videos:
- Everyone: Anyone can see your videos.
- Friends: Only your followers can see your videos.
- Only Me: Only you can see your videos.
4.4.3 Direct Message Settings
Direct message settings allow you to control who can send you direct messages.
4.4.4 Comment Filters
Comment filters allow you to filter comments based on keywords and phrases.
4.5 LinkedIn Privacy Settings
LinkedIn offers privacy settings to control who can see your profile, activity, and connections.
4.5.1 Profile Visibility
You can control who can see your profile:
- Public: Anyone can see your profile.
- Connections: Only your connections can see your profile.
- Private: Only you can see your profile.
4.5.2 Activity Broadcast
You can choose whether to broadcast your activity (such as liking, commenting, and sharing) to your network.
4.5.3 Who Can See Your Connections
You can choose who can see your connections:
- Your connections: Only your connections can see your connections.
- Only you: Only you can see your connections.
5. What Are the Best Apps to Keep My Photos Private?
Selecting the right apps to safeguard your photos is essential. These apps offer features like encryption, password protection, and private cloud storage to ensure your photos remain secure.
5.1 Keepsafe Photo Vault
Keepsafe Photo Vault is a popular app that offers password protection, encryption, and private cloud storage for your photos.
5.1.1 Key Features
- Password Protection: Protect your photos with a PIN, fingerprint, or facial recognition.
- Encryption: Encrypt your photos to prevent unauthorized access.
- Private Cloud Storage: Store your photos in Keepsafe’s private cloud.
- Fake PIN: Create a fake PIN to show a decoy vault if someone forces you to open the app.
- Break-In Alerts: Receive alerts if someone tries to break into your vault.
5.1.2 Pros and Cons
| Pros | Cons |
|---|---|
| Strong security features | Limited free storage |
| User-friendly interface | Requires subscription for full features |
| Private cloud storage option | Occasional performance issues |
| Fake PIN and break-in alerts |
5.2 Private Photo Vault
Private Photo Vault allows you to create multiple albums with individual passwords, providing an extra layer of security.
5.2.1 Key Features
- Multiple Albums: Create multiple albums with individual passwords.
- Password Protection: Protect your photos with a PIN or password.
- Decoy Password: Create a decoy password to show a fake vault.
- Break-In Reports: Receive reports of failed login attempts.
- Wi-Fi Photo Transfer: Transfer photos to and from your computer via Wi-Fi.
5.2.2 Pros and Cons
| Pros | Cons |
|---|---|
| Multiple albums with passwords | Ads in the free version |
| Decoy password feature | Limited free features |
| Wi-Fi photo transfer | Can be expensive for full features |
| Break-in reports |
5.3 Best Secret Folder
Best Secret Folder provides a decoy folder to hide your real private photos, adding an extra layer of deception.
5.3.1 Key Features
- Decoy Folder: Hide your real private photos behind a decoy folder.
- Password Protection: Protect your photos with a PIN or password.
- Fake PIN: Create a fake PIN to show a decoy vault.
- Stealth Mode: Hide the app icon from your home screen.
- Cloud Backup: Back up your photos to the cloud.
5.3.2 Pros and Cons
| Pros | Cons |
|---|---|
| Decoy folder for added security | Interface can be confusing |
| Stealth mode to hide the app icon | Cloud backup requires subscription |
| Fake PIN feature | Limited free features |
| Cloud backup option |
5.4 LockMyPix
LockMyPix encrypts your photos using AES encryption and offers a fake login feature, providing robust security.
5.4.1 Key Features
- AES Encryption: Encrypt your photos using AES encryption.
- Password Protection: Protect your photos with a PIN, password, or fingerprint.
- Fake Login: Create a fake login to show a decoy vault.
- Stealth Mode: Hide the app icon from your home screen.
- Cloud Backup: Back up your photos to the cloud.
5.4.2 Pros and Cons
| Pros | Cons |
|---|---|
| Strong AES encryption | Can be expensive for full features |
| Fake login for added security | Interface may not be intuitive for all |
| Stealth mode to hide the app icon | Cloud backup requires a subscription |
| Cloud backup option |
5.5 Vaulty
Vaulty allows you to hide photos and videos, and it also takes a snapshot of anyone who tries to access your vault with the wrong password.
5.5.1 Key Features
- Password Protection: Protect your photos with a PIN or password.
- Mugshot Feature: Takes a snapshot of anyone who enters the wrong password.
- Online Backup: Back up your photos to the cloud.
- Stealth Mode: Hide the app icon from your home screen.
- Multiple Vaults: Create multiple vaults with individual passwords.
5.5.2 Pros and Cons
| Pros | Cons |
|---|---|
| Mugshot feature for added security | Online backup requires subscription |
| Stealth mode to hide the app icon | Interface can feel outdated |
| Multiple vaults for organization | Limited free features |
| Online backup option |
6. How Do Cloud Storage Services Ensure Photo Privacy?
Cloud storage services employ various security measures to ensure the privacy of your photos, including encryption, access controls, and compliance with privacy regulations.
6.1 Encryption
Encryption is a fundamental security measure used by cloud storage services to protect your photos from unauthorized access.
6.1.1 Encryption in Transit
Cloud storage services encrypt your photos while they are being uploaded to or downloaded from their servers, protecting them from interception.
6.1.2 Encryption at Rest
Cloud storage services encrypt your photos while they are stored on their servers, ensuring that they cannot be accessed by unauthorized individuals.
6.2 Access Controls
Access controls limit who can view your photos, ensuring that only authorized individuals have access.
6.2.1 User Authentication
Cloud storage services require you to authenticate your identity with a username and password or biometric authentication before you can access your photos.
6.2.2 Permissions
Cloud storage services allow you to set permissions for your photos and albums, controlling who can view, edit, or share them.
6.3 Privacy Policies
Cloud storage services have privacy policies that outline how they collect, use, and protect your personal information, including your photos.
6.3.1 Reviewing Privacy Policies
It’s essential to review the privacy policies of cloud storage services to understand how they handle your photos and what rights you have.
6.3.2 GDPR and CCPA Compliance
Many cloud storage services comply with privacy regulations like GDPR and CCPA, which give you greater control over your personal data.
6.4 Security Audits
Cloud storage services undergo regular security audits to ensure that their security measures are effective and up-to-date.
6.4.1 Third-Party Audits
Some cloud storage services undergo third-party audits to verify their security and compliance.
6.4.2 Security Certifications
Cloud storage services may obtain security certifications like ISO 27001 and SOC 2 to demonstrate their commitment to security.
6.5 Physical Security
Cloud storage services invest in physical security measures to protect their data centers from unauthorized access and physical threats.
6.5.1 Data Center Security
Data centers are equipped with security measures like surveillance cameras, biometric access controls, and on-site security personnel.
6.5.2 Redundancy and Disaster Recovery
Cloud storage services use redundancy and disaster recovery measures to ensure that your photos are protected from data loss due to hardware failures, natural disasters, or other incidents.
6.6 Data Retention Policies
Cloud storage services have data retention policies that outline how long they store your photos and what happens to them when you delete your account.
6.6.1 Understanding Data Retention Policies
It’s essential to understand the data retention policies of cloud storage services to know how long your photos will be stored and what happens to them after you delete your account.
7. What Should I Do if My Photos Are Leaked?
If your photos are leaked, taking immediate action is crucial to minimize the damage. This includes securing your accounts, seeking legal advice, and monitoring the internet for unauthorized use of your images.
7.1 Secure Your Accounts
Immediately secure your accounts to prevent further unauthorized access.
7.1.1 Change Passwords
Change the passwords for all your accounts, including social media, email, and cloud storage.
7.1.2 Enable Two-Factor Authentication
Enable two-factor authentication for all your accounts to add an extra layer of security.
7.1.3 Review Account Activity
Review your account activity to identify any suspicious behavior.
7.2 Contact the Platforms
Contact the platforms where your photos were leaked to request their removal.
7.2.1 Reporting to Social Media Platforms
Report the leaked photos to social media platforms like Facebook, Instagram, and Twitter.
7.2.2 Reporting to Cloud Storage Services
Report the leaked photos to cloud storage services like Google Photos, iCloud Photos, and Dropbox.
7.3 Seek Legal Advice
Seek legal advice to understand your rights and options.
7.3.1 Consulting with a Lawyer
Consult with a lawyer who specializes in privacy and data protection.
7.3.2 Sending Cease and Desist Letters
Your lawyer can send cease and desist letters to individuals or organizations that are distributing your photos.
7.4 Monitor the Internet
Monitor the internet for unauthorized use of your photos.
7.4.1 Using Reverse Image Search
Use reverse image search tools like Google Images and TinEye to find where your photos are being used online.
7.4.2 Setting Up Google Alerts
Set up Google Alerts to receive notifications when your name or photos are mentioned online.
7.5 Contact Law Enforcement
Contact law enforcement if you believe your photos were leaked as a result of a crime.
7.5.1 Reporting to the Police
Report the incident to the police and provide them with any evidence you have.
7.5.2 Filing a Complaint with the FTC
File a complaint with the Federal Trade Commission (FTC) if you believe your privacy rights have been violated.
7.6 Notify Affected Individuals
Notify individuals who are depicted in the leaked photos to inform them of the breach.
7.6.1 Contacting Friends and Family
Contact friends and family who are depicted in the leaked photos to inform them of the breach and provide support.
7.6.2 Offering Support and Assistance
Offer support and assistance to individuals who are affected by the breach.
7.7 Consider Public Relations
Consider public relations to manage the fallout from the leak.
7.7.1 Hiring a Public Relations Firm
Hire a public relations firm to help you manage the media and control the narrative.
7.7.2 Preparing a Statement
Prepare a statement to address the leak and communicate your response.
8. What Are the Legal Aspects of Photo Privacy?
Understanding the legal aspects of photo privacy is essential for protecting your rights and ensuring compliance with privacy laws.
8.1 Copyright Law
Copyright law protects your ownership of your photos, giving you the exclusive right to control how they are used.
8.1.1 Registering Your Copyright
Register your copyright with the U.S. Copyright Office to strengthen your legal rights.
8.1.2 Using Copyright Notices
Use copyright notices on your photos to assert your ownership.
8.2 Privacy Laws
Privacy laws protect your right to control your personal information, including your photos.
8.2.1 GDPR
The General Data Protection Regulation (GDPR) is a European Union law that protects the personal data of EU citizens.
8.2.2 CCPA
The California Consumer Privacy Act (CCPA) is a California law that gives California residents greater control over their personal data.
8.2.3 Other State Privacy Laws
Many other states have privacy laws that protect your personal information.
8.3 Defamation Law
Defamation law protects you from false and defamatory statements that harm your reputation.
8.3.1 Libel and Slander
Libel is written defamation, while slander is spoken defamation.
8.3.2 Proving Defamation
To prove defamation, you must show that the statement was false, published to a third party, and caused you harm.
8.4 Right of Publicity
The right of publicity protects your right to control the commercial use of your name and likeness.
8.4.1 Unauthorized Use of Your Image
If someone uses your image for commercial purposes without your permission, you may have a claim for violation of your right of publicity.
8.4.2 Obtaining Consent
Obtain consent from individuals before using their images for commercial purposes.
8.5 Data Breach Laws
Data breach laws require organizations to notify individuals when their personal information is compromised in a data breach.
8.5.1 Notification Requirements
Data breach laws typically require organizations to notify affected individuals within a certain timeframe and provide them with information about the breach.
8.5.2 Remedies
Data breach laws may provide remedies for affected individuals, such as monetary damages and credit monitoring services.
8.6 Child Online Privacy Protection Act (COPPA)
The Child Online Privacy Protection Act (COPPA) protects the online privacy of children under the age of 13.
8.6.1 Parental Consent
COPPA requires websites and online services to obtain parental consent before collecting personal information from children under the age of 13.
8.6.2 Restrictions on Data Collection
COPPA imposes restrictions on the collection, use, and disclosure of children’s personal information.
9. How Can I Permanently Delete Photos from My Devices?
Permanently deleting photos from your devices is essential to ensure they cannot be recovered. This involves more than just deleting them from your gallery; it requires securely erasing the data.
9.1 Deleting Photos from Your Gallery
Deleting photos from your gallery is the first step, but it doesn’t permanently erase the data.
9.1.1 Emptying the Trash or Recycle Bin
After deleting photos from your gallery, empty the trash or recycle bin to remove them from your device.
9.1.2 Overwriting Deleted Data
Overwriting deleted data with new data makes it more difficult to recover the original photos.
9.2 Using Secure Deletion Software
Secure deletion software overwrites the data multiple times, making it virtually impossible to recover.
9.2.1 DBAN (Darik’s Boot and Nuke)
DBAN is a free and open-source tool for securely wiping hard drives.
9.2.2 Eraser
Eraser is a free tool for securely deleting files and folders on Windows.
9.3 Encrypting Your Device
Encrypting your device before deleting photos makes it more difficult for unauthorized individuals to access the data.
9.3.1 Enabling Encryption on iOS
Enable encryption on your iOS device by setting a passcode.
9.3.2 Enabling Encryption on Android
Enable encryption on your Android device in the security settings.
9.4 Factory Resetting Your Device
Factory resetting your device erases all data, including photos, but it may not be sufficient to prevent data recovery.
9.4.1 Performing a Factory Reset on iOS
Perform a factory reset on your iOS device in the settings menu.
9.4.2 Performing a Factory Reset on Android
Perform a factory reset on your Android device in the settings menu.
9.5 Physically Destroying Storage Media
Physically destroying storage media is the most secure way to prevent data recovery.
9.5.1 Shredding Hard Drives
Shredding hard drives with a specialized shredder makes it impossible to recover the data.
9.5.2 Degaussing Hard Drives
Degaussing hard drives with a degausser erases the data by disrupting the magnetic field.
9.5.3 Destroying USB Drives and SD Cards
Destroying USB drives and SD cards with a hammer or shredder makes it impossible to recover the data.
9.6 Overwriting Free Space
Overwriting free space on your device with new data makes it more difficult to recover deleted photos.
9.6.1 Using Disk Utility on Mac
Use Disk Utility on Mac to erase free space on your hard drive.
9.6.2 Using Third-Party Tools on Windows
Use third-party tools like CCleaner to erase free space on your Windows computer.
10. How to Back Up Your Photos Securely?
Backing up your photos securely ensures that you have a copy of your images in case of data loss, while also protecting them from unauthorized access.
10.1 Encrypting Your Backups
Encrypting your backups protects your photos from unauthorized access if the backup media is lost or stolen.
10.1.1 Using Encryption Software
Use encryption software like VeraCrypt to encrypt your backups.
10.1.2 Using Built-In Encryption Features
Use built-in encryption features in backup software like Time Machine on Mac.
10.2 Storing Backups in a Secure Location
Storing backups in a secure location protects them from physical threats like theft, fire, and natural disasters.
10.2.1 Off-Site Storage
Store backups in an off-site location, such as a safe deposit box or